What Are The Security Risks For Clients Using A Cloud-based Service
Organizations continue to develop new applications in or migrate existing applications to cloud-based services. The federal regime recently made deject-adoption a central tenet of its It modernization strategy. An arrangement that adopts cloud technologies and/or chooses cloud service providers (CSP)due south and services or applications without becoming fully informed of the risks involved exposes itself to a myriad of commercial, financial, technical, legal, and compliance risks. In this blog post, we outline 12 risks, threats, and vulnerabilities that organizations face when moving application or data to the cloud. In our follow-up post, Best Practices for Deject Security, nosotros explore a series of best practices aimed at helping organizations securely move data and applications to the cloud.
Nosotros would like to note that the threats and vulnerabilities involved in migrating to the deject are always-evolving, and the ones listed here are by no means exhaustive. Information technology is important to consider other challenges and risks associated with cloud adoption specific to their missions, systems, and data.
The National Constitute of Standards and Engineering science (NIST) cloud model provides a definition of cloud computing and how it tin can be used and deployed.
NIST identifies the following characteristics and models for deject calculating:
- Essential characteristics: on-demand self-service, broad network access, resource pooling, rapid elasticity, and measured service
- Service Models: software as a service (SaaS), platform as a service (PaaS), and infrastructure every bit a service (IaaS)
- Deployment Models: individual deject, customs cloud, public cloud, and hybrid cloud
Cloud Computing Threats, Risks, and Vulnerabilities
Deject environments experience--at a loftier level--the same threats as traditional information centre environments; the threat picture is the aforementioned. That is, cloud computing runs software, software has vulnerabilities, and adversaries endeavour to exploit those vulnerabilities. Still, different information applied science systems in a traditional information heart, in cloud computing, responsibility for mitigating the risks that result from these software vulnerabilities is shared between the CSP and the deject consumer. As a result, consumers must understand the division of responsibilities and trust that the CSP meets their responsibilities. Based on our literature searches and analysis efforts, the following list of cloud-unique and shared cloud/on-premise vulnerabilities and threats were identified. The figure below also details the threat picture for cloud computing platforms.
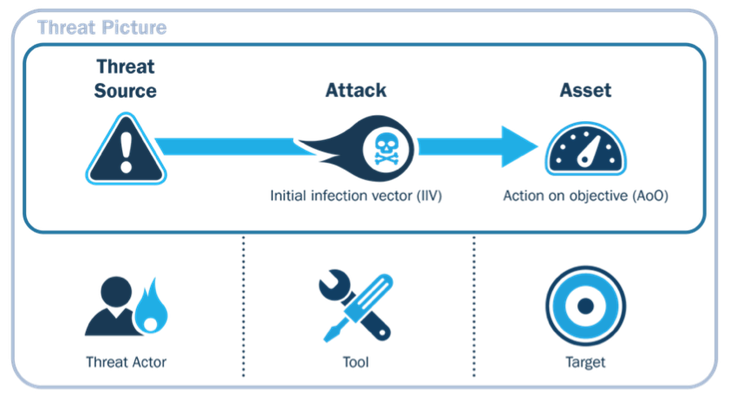
Deject-Unique Threats and Risks
The following vulnerabilities are a result of a CSP'southward implementation of the five deject computing characteristics. These vulnerabilities do not be in archetype IT information centers.
#ane Consumers Have Reduced Visibility and Control. When transitioning avails/operations to the deject, organizations lose some visibility and control over those assets/operations. When using external cloud services, the responsibleness for some of the policies and infrastructure moves to the CSP.
The actual shift of responsibleness depends on the cloud service model(s) used, leading to a image shift for agencies in relation to security monitoring and logging. Organizations demand to perform monitoring and analysis of information virtually applications, services, data, and users, without using network-based monitoring and logging, which is bachelor for on-premises Information technology.
#ii On-Need Self Service Simplifies Unauthorized Use. CSPs make information technology very piece of cake to provision new services. The on-need self-service provisioning features of the cloud enable an organization'southward personnel to provision additional services from the bureau's CSP without Information technology consent. The exercise of using software in an organisation that is non supported past the organization'south IT section is commonly referred to as shadow Information technology.
Due to the lower costs and ease of implementing PaaS and SaaS products, the probability of unauthorized use of deject services increases. Even so, services provisioned or used without It's cognition present risks to an organization. The use of unauthorized deject services could consequence in an increase in malware infections or data exfiltration since the organization is unable to protect resource information technology does not know about. The utilize of unauthorized cloud services besides decreases an organization'southward visibility and control of its network and data.
#3 Internet-Accessible Management APIs can be Compromised. CSPs expose a set up of application programming interfaces (APIs) that customers use to manage and interact with cloud services (likewise known as the direction aeroplane). Organizations use these APIs to provision, manage, orchestrate, and monitor their avails and users. These APIs can incorporate the same software vulnerabilities as an API for an operating system, library, etc. Different management APIs for on-premises computing, CSP APIs are accessible via the Net exposing them more broadly to potential exploitation.
Threat actors wait for vulnerabilities in direction APIs. If discovered, these vulnerabilities tin be turned into successful attacks, and system cloud assets can be compromised. From there, attackers can apply organisation avails to perpetrate farther attacks against other CSP customers.
#4 Separation Amid Multiple Tenants Fails. Exploitation of arrangement and software vulnerabilities inside a CSP'south infrastructure, platforms, or applications that support multi-tenancy tin lead to a failure to maintain separation among tenants. This failure can be used by an aggressor to gain access from i organization'southward resource to another user's or organization's assets or information. Multi-tenancy increases the set on surface, leading to an increased chance of data leakage if the separation controls fail.
This assail can be accomplished by exploiting vulnerabilities in the CSP's applications, hypervisor, or hardware, subverting logical isolation controls or attacks on the CSP'due south direction API. To engagement, there has not been a documented security failure of a CSP's SaaS platform that resulted in an external attacker gaining access to tenants' data.
No reports of an attack based on logical separation failure were identified; however, proof-of-concept exploits have been demonstrated.
#v Data Deletion is Incomplete. Threats associated with data deletion exist because the consumer has reduced visibility into where their data is physically stored in the cloud and a reduced power to verify the secure deletion of their data. This risk is concerning because the information is spread over a number of different storage devices within the CSP'southward infrastructure in a multi-tenancy environment. In addition, deletion procedures may differ from provider to provider. Organizations may not be able to verify that their data was securely deleted and that remnants of the data are not available to attackers. This threat increases as an agency uses more CSP services.
Deject and On-Premise Threats and Risks
The post-obit are risks that employ to both cloud and on-premise IT data centers that organizations demand to address.
#six Credentials are Stolen. If an attacker gains access to a user's deject credentials, the attacker tin have admission to the CSP's services to provision additional resources (if credentials immune admission to provisioning), equally well as target the organization'southward assets. The aggressor could leverage cloud computing resources to target the organization'due south administrative users, other organizations using the same CSP, or the CSP's administrators. An assailant who gains access to a CSP administrator'southward cloud credentials may exist able to use those credentials to access the agency's systems and data.
Ambassador roles vary between a CSP and an system. The CSP ambassador has access to the CSP network, systems, and applications (depending on the service) of the CSP's infrastructure, whereas the consumer's administrators have admission merely to the organization'due south cloud implementations. In essence, the CSP administrator has assistants rights over more than than one client and supports multiple services.
#7 Vendor Lock-In Complicates Moving to Other CSPs. Vendor lock-in becomes an event when an organisation considers moving its assets/operations from ane CSP to another. The organization discovers the cost/effort/schedule fourth dimension necessary for the move is much higher than initially considered due to factors such as non-standard data formats, not-standard APIs, and reliance on 1 CSP's proprietary tools and unique APIs.
This issue increases in service models where the CSP takes more responsibility. Equally an agency uses more features, services, or APIs, the exposure to a CSP'south unique implementations increases. These unique implementations crave changes when a adequacy is moved to a unlike CSP. If a selected CSP goes out of business organisation, it becomes a major problem since data tin be lost or cannot be transferred to another CSP in a timely manner.
#8 Increased Complexity Strains Information technology Staff. Migrating to the cloud tin can introduce complication into IT operations. Managing, integrating, and operating in the deject may crave that the agency's existing IT staff learn a new model. IT staff must have the chapters and skill level to manage, integrate, and maintain the migration of assets and data to the cloud in add-on to their current responsibilities for on-bounds IT.
Key management and encryption services become more than circuitous in the deject. The services, techniques, and tools available to log and monitor cloud services typically vary across CSPs, further increasing complication. In that location may besides be emergent threats/risks in hybrid deject implementations due to technology, policies, and implementation methods, which add together complexity. This added complexity leads to an increased potential for security gaps in an agency's cloud and on-premises implementations.
#nine Insiders Abuse Authorized Admission. Insiders, such as staff and administrators for both organizations and CSPs, who abuse their authorized access to the arrangement's or CSP'southward networks, systems, and data are uniquely positioned to cause damage or exfiltrate information.
The affect is well-nigh likely worse when using IaaS due to an insider's power to provision resources or perform nefarious activities that require forensics for detection. These forensic capabilities may not be available with deject resources.
#10 Stored Data is Lost. Data stored in the cloud can be lost for reasons other than malicious attacks. Adventitious deletion of data by the cloud service provider or a concrete ending, such every bit a burn down or convulsion, can lead to the permanent loss of customer data. The burden of avoiding data loss does not fall solely on the provider'south shoulders. If a customer encrypts its information before uploading information technology to the cloud simply loses the encryption key, the information will be lost. In addition, inadequate understanding of a CSP'southward storage model may result in data loss. Agencies must consider information recovery and be prepared for the possibility of their CSP existence acquired, irresolute service offerings, or going bankrupt.
This threat increases equally an agency uses more than CSP services. Recovering data on a CSP may exist easier than recovering it at an agency because an SLA designates availability/uptime percentages. These percentages should exist investigated when the agency selects a CSP.
#11 CSP Supply Chain is Compromised. If the CSP outsources parts of its infrastructure, operations, or maintenance, these 3rd parties may not satisfy/support the requirements that the CSP is contracted to provide with an arrangement. An organization needs to evaluate how the CSP enforces compliance and check to see if the CSP flows its own requirements downwards to 3rd parties. If the requirements are not being levied on the supply concatenation, and so the threat to the agency increases.
This threat increases as an organization uses more CSP services and is dependent on individual CSPs and their supply chain policies.
#12 Bereft Due Diligence Increases Cybersecurity Run a risk. Organizations migrating to the deject often perform bereft due diligence. They move data to the cloud without understanding the full scope of doing so, the security measures used by the CSP, and their own responsibility to provide security measures. They make decisions to use cloud services without fully understanding how those services must be secured.
Wrapping Upwardly and Looking Ahead
It is important to think that CSPs use a shared responsibility model for security. The CSP accepts responsibility for some aspects of security. Other aspects of security are shared between the CSP and the consumer. Finally, some aspects of security remain the sole responsibility of the consumer. Effective cloud security depends on knowing and meeting all consumer responsibilities. Consumers' failure to understand or meet their responsibilities is a leading crusade of security incidents in cloud-based systems.
In this blog post, we take identified five cloud-unique and seven cloud and on-bounds threats that organizations face equally they consider migrating their data and assets to the cloud. In the adjacent post in this series, we will explore a serial of best practices aimed at helping organizations deeply move data and applications to the deject.
Additional Resources
Read the next post in this series, Best Practices for Cloud Security .
For more information about cloud calculating security, delight visit the following sites:
The Federal Gamble and Authorization Direction Programme (FedRAMP) is a government-wide program that provides a standardized arroyo to security assessment, authorisation, and continuous monitoring for cloud products and services.
The Deject Security Alliance works to promote the use of best practices for providing security balls within Cloud Computing, and provide pedagogy on the uses of Deject Computing to assistance secure all other forms of computing
The European Spousal relationship Agency for Network and Information Security (ENISA)'due south page on cloud security.
What Are The Security Risks For Clients Using A Cloud-based Service,
Source: https://insights.sei.cmu.edu/blog/12-risks-threats-vulnerabilities-in-moving-to-the-cloud/
Posted by: nicholsalwat1946.blogspot.com


0 Response to "What Are The Security Risks For Clients Using A Cloud-based Service"
Post a Comment